In this article, we present a realization of Boson Consensus — Collaborative Mining, where rootchain and sharded blockchains use proof-of-work (PoW) consensus:
- The rootchain runs PoW, and each root block collects the headers/hashes of the blocks from sharded blockchains. As agreed by the consensus of rootchain, the corresponding blocks of each sharded blockchain in the rootchain must be a valid chain of the shard.
- A list of sharded blockchains processes their transactions and produces blocks relatively-independently. We assume the sharded blockchain uses PoW to illustrate collaborative mining, however, as mentioned in the previous article (Part 4), sharded blockchains could use other consensuses (PoS, dPoS) in addition to PoW as well.
The main purpose of collaborative mining is to increase the scalability of PoW-based blockchains by increasing the number of sharded blockchains. In addition, collaborative mining could also greatly enhance the security of blockchains via a technique called hashpower reuse technique . The hashpower reuse technique is motivated by the similar concept in software development — code reuse, where a common good practice in software development is to reuse high-quality existing code (e.g., standard library) rather than reinvent the wheel. Similarly, Collaborative Mining enables the hashpower reuse technique so that multiple sharded blockchains reuse the same hashpower of the rootchain (which has strong hashpower due to high mining rewards) to resist double-spending attacks.
In the following, we will discuss the details of collaborative mining. We will first illustrate 51% attack, a.k.a, double-spending attack on PoW consensus and clarify some misunderstandings via recent BTG/ETC attack. Then, we will present how hashpower reuse technique could help increase the security for blockchains, and we will present further security concerns of collaborative mining.
51% Attack: Misunderstanding and Facts
The most famous attack on PoW consensus is probably double-spending attack — an attacker could arbitrarily revert a block (and thus revert one or more transactions) by secretly mining a longer attacking fork as long as the attacker has more than 51% hashpower of the network. Although 51% hashpower of the network seems to be a strong requirement if the network’s hashpower is decentralized (e.g., Bitcoin never suffers from 51% attack), recently a lot of PoW blockchains have been double-spending attacked:
- BTG was attacked in May 2018, where $18.6 million may have been double-spent
- ETC was attacked in January 2019, where $1 million may have been double-spent
Note that these two cryptocurrency market caps are in top 30 in coinmarketcap and have considerable amount of hashpower. This implies that those PoW blockchains whose market cap rank is after 30th will be even more vulnerable to 51% attack.
Why are some of the blockchains more vulnerable to double-spending attack while some of the blockchains are more resistant, even though the attack still needs 51% hashpower of the network? One key misunderstanding of 51% attack is the definition of the total hashpower of the network, which could be:
- All hashpower of the miners that are contributing to the blockchain; or
- All hashpower of the miners running the same hash algorithm (e.g., running Ethash); or
- All hashpower of the miners that could effectively contribute the hashpower (e.g., all miners own GPU for ETC, but they may mine Equihash or CryptoNight);
- All hashpower from all computational resources in the world (including super-computers).
Most of the time, people use the first definition when referring to 51%. However, with more blockchains running the same hash algorithms (e.g., BTC/BCH, ETH/ETC) and being mined by shared hardware (GPUs), we have to consider a more general definition of the hashpower of the network, whereby following the definition 2 or 3, an attack could double spend a transaction with much lower hashpower than 51% of the network .
Fact 1: Only 5.2% of the ETH hashpower can perform a double-spending attack on ETC (As of Jan. 21, 2019)
Let us take ETC as an example. Suppose the ETC’s hashpower is 9Th/s. Following Definition 1, 51% attack succeeds only if 51% of the existing 9Th/s miners are malicious. However, by Definition 2, since ETH is also running Ethash (the same as ETC) and has 176Th/s, an attacker from ETH miners can perform the attack by only moving 9Th/s from ETH to ETC, and such attack only takes 9/176=5.2% of the hashpower of ETH, which is much lower than so-called 51%.
Fact 2: Double spending some PoW blockchains may only take hundreds of dollars
The security issue becomes more severe with the presence of hashpower marketplace (such as NiceHash), where an attacker could rent hashpower for a short period of time and perform an attack. https://www.crypto51.app/ provides a list of PoW blockchains that could be attacked by renting hashpower from NiceHash, and the cost is just a few hundred dollars.
A screenshot from www.crypto51.app
Hashpower reuse technique
A key observation from this list is that BTC/ETH has very strong hashpower but with lower number of transactions per second. Is it possible that new blockchains could reuse the hashpower of BTC/ETH to prevent double-spending attacks, like code reuse in software development? One possible solution is to use sidechains, where the block producers (BP) of the sidechain periodically submit their chain snapshot to the mainchain (BTC/ETH). However, the consensus of the mainchain is not aware of the underlying sidechain consensus, and thus if different views are created in the sidechain, i.e., forks, the sidechain has to decide the correct view by the sidechain’s own consensus algorithm, which weakens the security model.
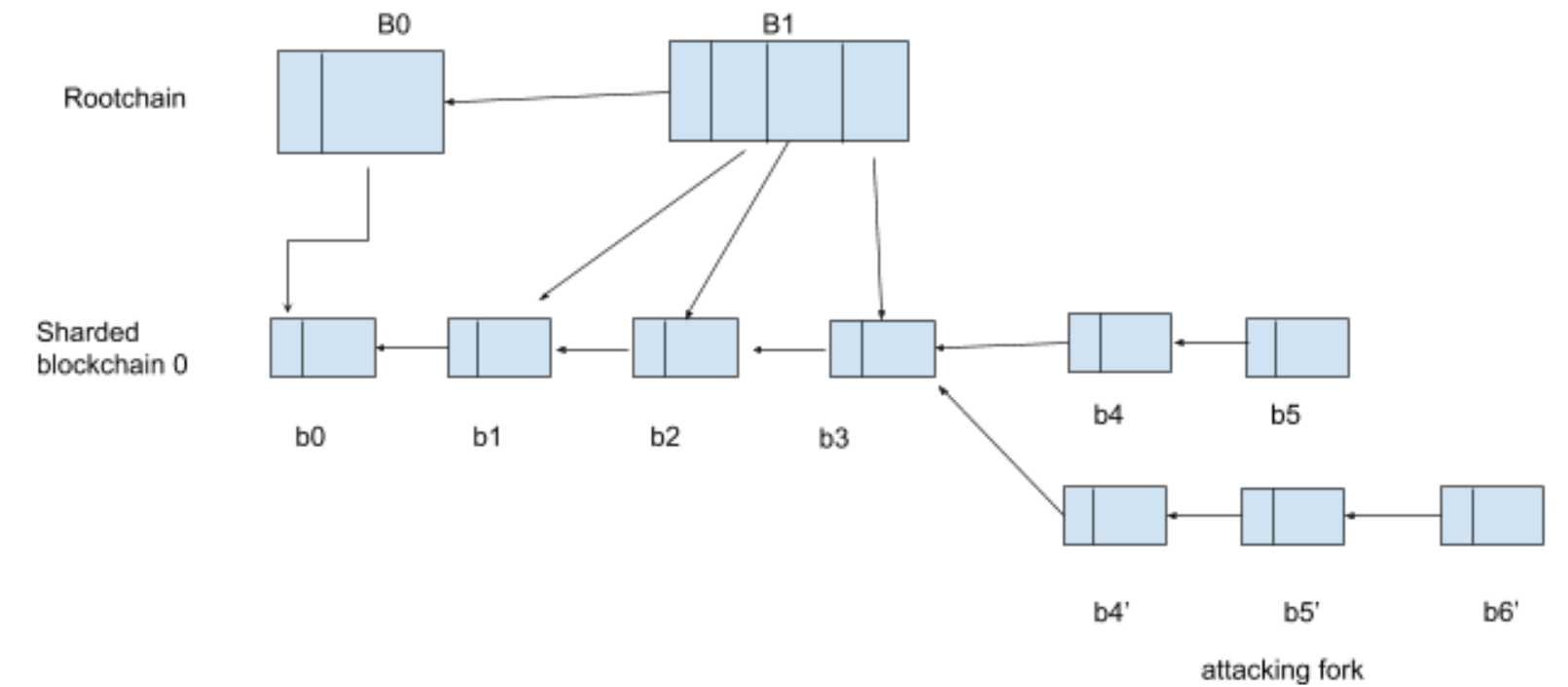
Hashpower reuse technique proposed by QuarkChain addresses this problem. The rootchain of Boson Consensus algorithm is aware of the consensus of the underlying sharded blockchains (note that the sharded blockchains may run different consensus algorithms other than PoW), and include one valid chain/fork of each sharded blockchain in the root blocks by putting the block headers/hashes in root blocks. In other words, the rootchain describes the canonical chains of all sharded blockchains via their headers/hashes, and all sharded blockchains follow the canonical chains defined by rootchain because sharded blockchains are running root-chain-first fork choice rule. With the consensus established between rootchain and sharded blockchains, any double-spending attack on a shard block that is already included in rootchain has to also revert the root blocks, which requires 51% hashpower of the rootchain .
An example of a double-spending attack in QuarkChain
In addition, to incentivize the miners of the rootchain to include sharded blocks into root blocks, part of the miners’ rewards of sharded blocks will be contributed to the root blocks and thus collected by the rootchain miners, called tax. For example, if the tax rate is 50%, it means that miners of sharded blocks will collect half of the sharded miner reward, and the rootchain miners will collect as much as sharded blocks (the longest fork) to maximize its tax. As a result, we would expect higher hashpower on rootchain because of higher miners’ rewards
Attack Vectors
Besides double-spending attack, collaborative mining and hashpower reuse technique open the possibilities of several other attacks. We summarize the attacks as follows:
Blacklist attack by sharded blockchain miners
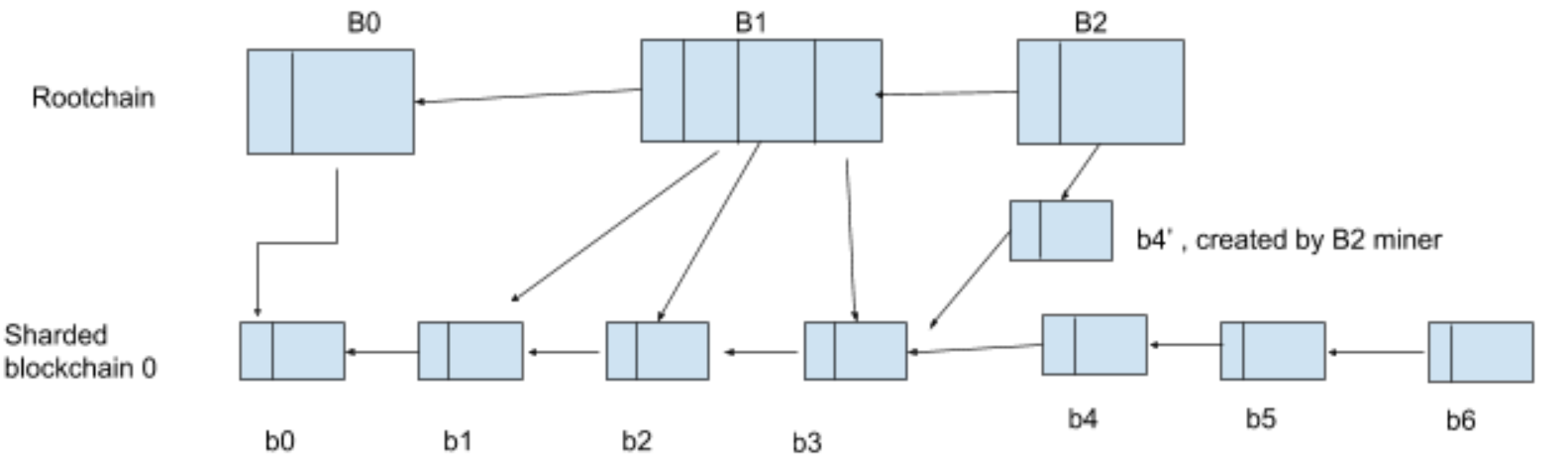
By using 51% hashpower of one shard, an attacker may intentionally exclude some transactions from a user and the corresponding block by creating a longer fork and reverting the block before the sharded block is included in the root block. Note that this attack could also happen for the existing chains with weak hashpower, and the attacker must constantly exclude the blocks that contain the transaction from the user until all other miners stop including that transaction. In addition, the attack would require much higher hashpower once the sharded block including the transaction is included in a root block.
An example of a blacklist attack by sharded blockchain miners
Blacklist attack by rootchain miners
When packing the root blocks, a rootchain miner could exclude some blocks (not included in previous root blocks) of a sharded chain by including another a fork created by itself. This means that the rootchain has to spend extra hashpower to create attacking fork while collecting less mining reward if the fork to be attacked is longer.
An example of a blacklist attack by rootchain miners
Bribery attack
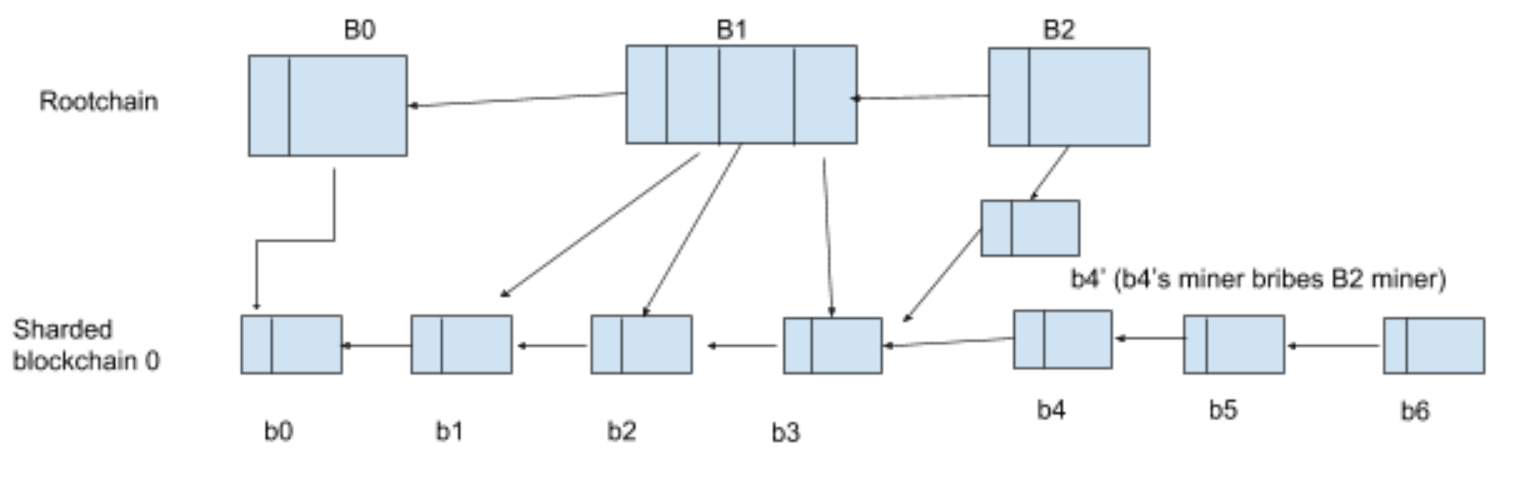
When a sharded chain has two forks, one of which will be included in the next root block, a rootchain miner should include the longer fork to maximize its block reward. However, if the miners of the shorter fork bribe the rootchain miners, the rootchain miners may include the shorter fork. This attack highly depends on the tax rate and the decentralized level of rootchain:
- Suppose tax rate is 50%, the shorter fork should be more than half of the longer fork if all rewards of the short fork are used to bribe the rootchain miners.
- If the rootchain miners are decentralized enough, it would be much more challenging to bribe major rootchain miners to execute bribery attack.
An example of bribery attack
Summary
In this article, we clarified some misunderstandings of 51% attack and listed some facts of attacking cost. Inspired by code reuse in software development, we then proposed a technology called hashpower reuse technique in the context of blockchain sharding to enhance the security of blockchains. We described how Boson Consensus and Collaborative Mining enable hashpower reuse, and we summarized the potential attack vectors.